Deploying & Scanning with Qualys Cloud Agent
In this method of vulnerability scanning, an agent application is installed on a host. the agent application is then in charge of scanning and reporting results of scans back the Qualys cloud servers. Organizations can then take action on the results, remediating out of date software and adjusting any settings that may be making the host vulnerable to threat actor attack.
Installation
To install the Qualys cloud agent software on a Windows host navigate to the Qualys dashboard and click on the modules drop down in the top right of the page and select Cloud Agent.
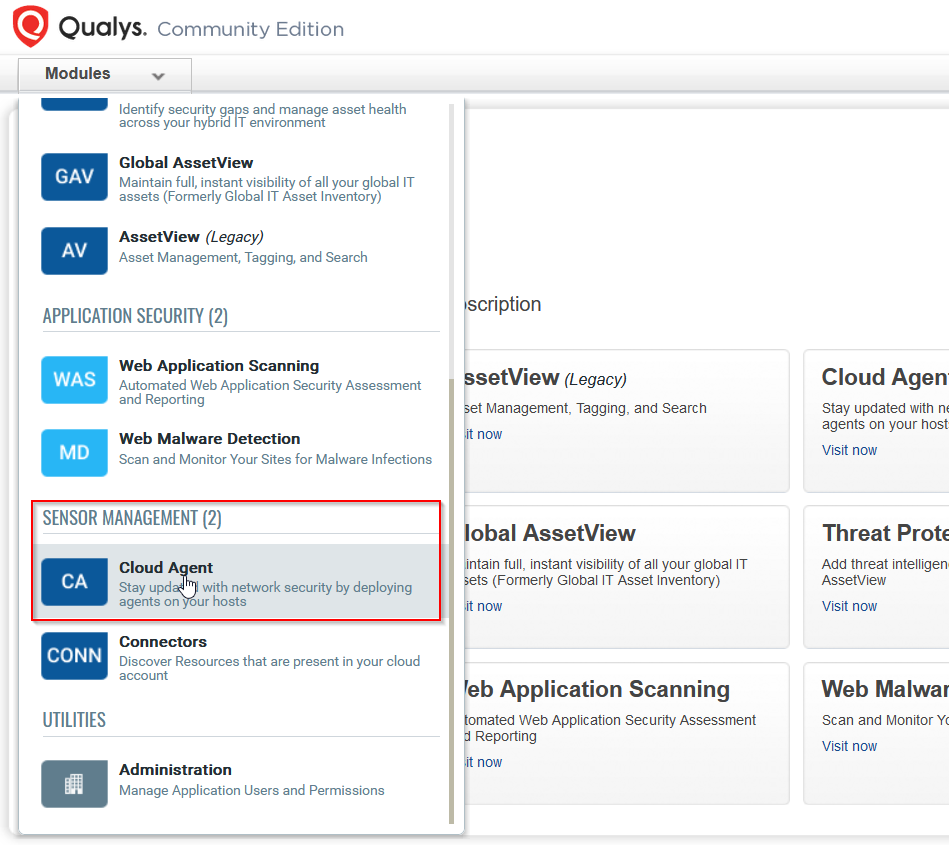
Click on Download & Install Agents.
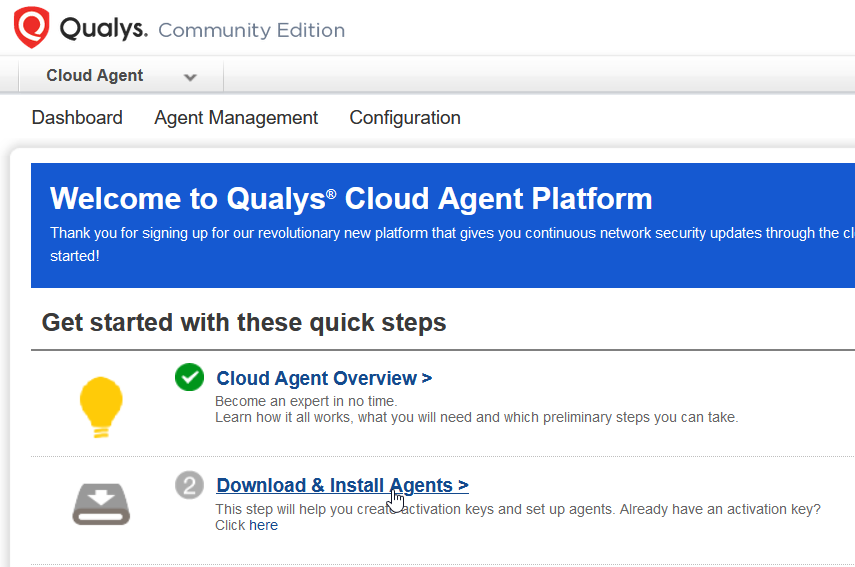
Now give our cloud agent/ activation key a name, in my case I will be calling this agent Vulnerable Windows 10. I also selected provision key for the agent, the community edition comes with 20 licenses for agents and devices.
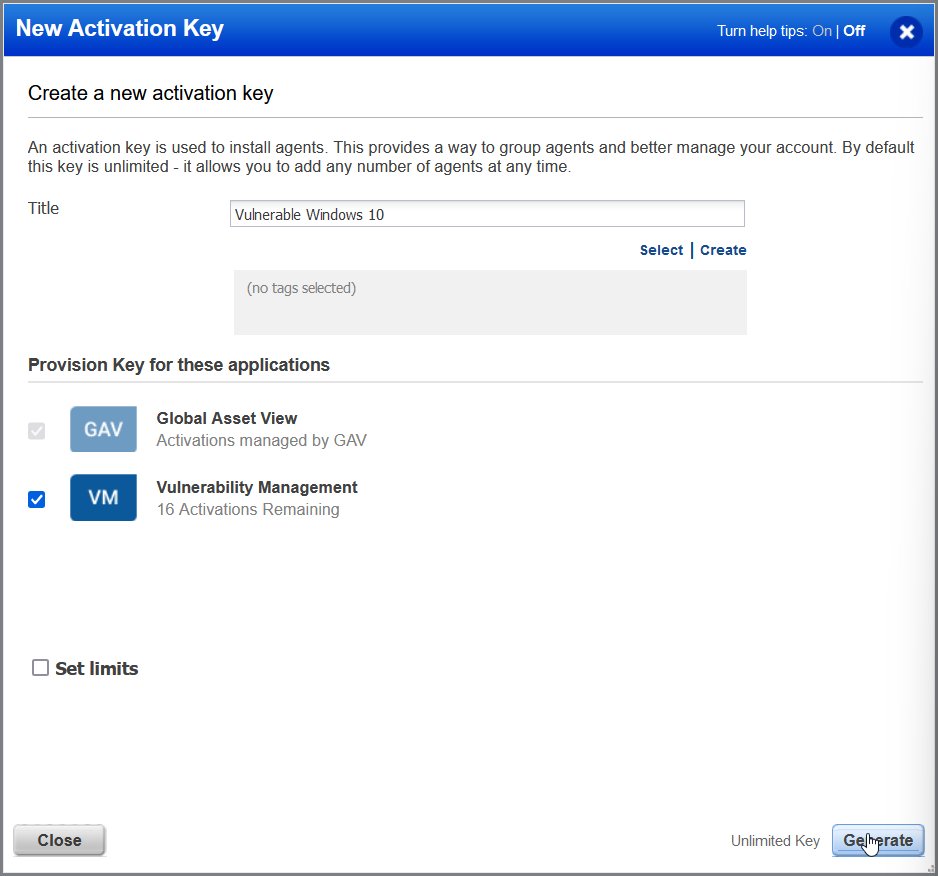
Hit generate and you will be presented with a list of platforms to install the cloud agent software on. In my case I will be selecting Windows. Then an activation key will be generated and a Windows cmd command will be presented that needs to be run to install the agent application. Note: The agent application can not be installed without the cmd command.
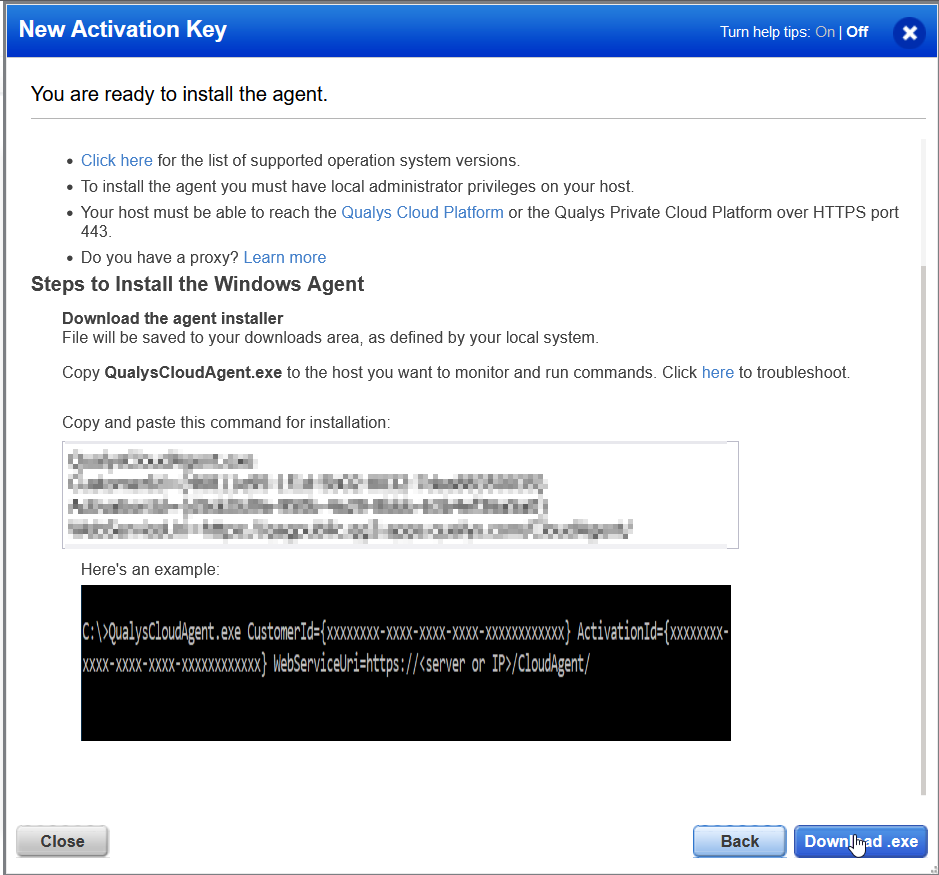
Back at our vulnerable Windows 10 VM I have transferred the Qualys agent installer to the machine and also a text file that contains the cmd command for installation. We need to run cmd prompt as admin to get this to install correctly as the agent needs elevated privileges on the systems that it runs on to carry out scanning and reporting.
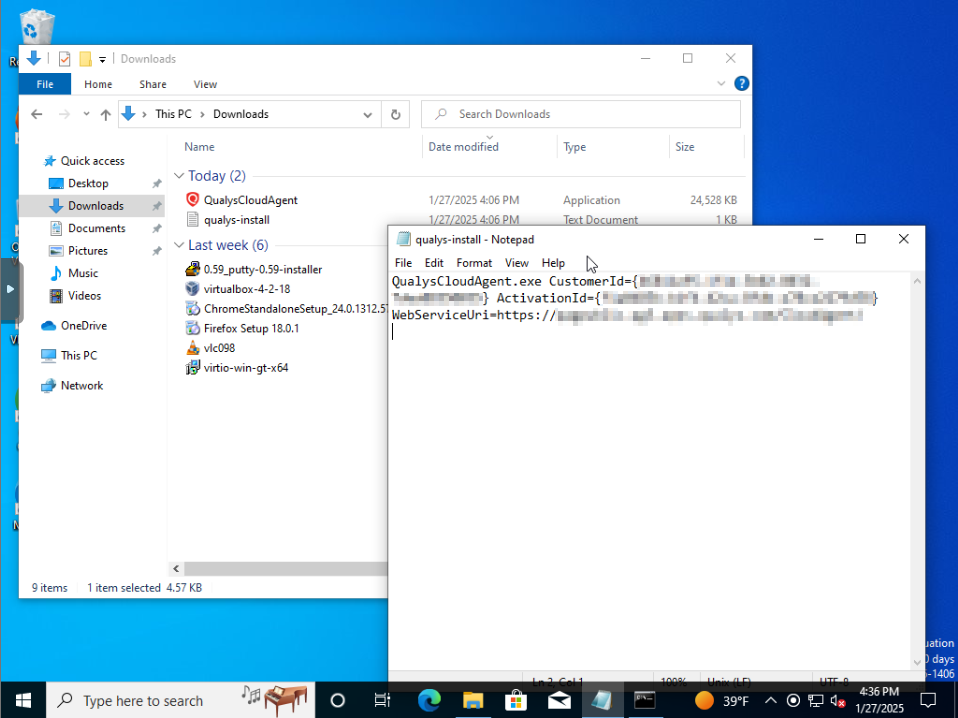
And here we are installing the software from cmd prompt. Install finished successfully.
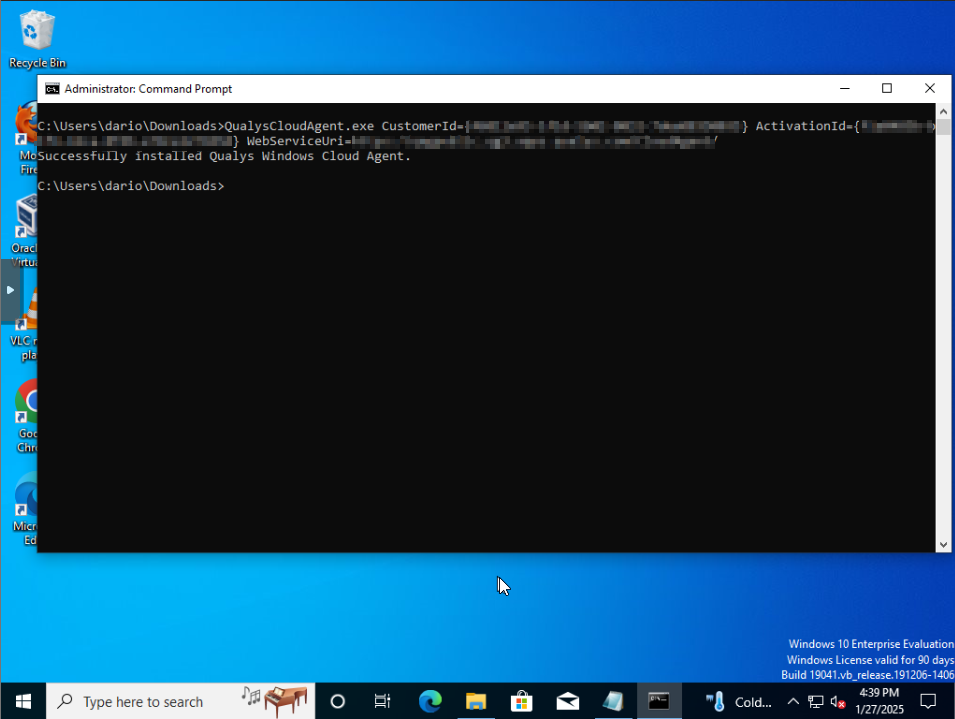
Now in theory we should be able to see our agent reporting that it's connected and successfully phoning back home to Qualys. Checking back at Qualys, it's confirmed we have our agent reporting back, the key we used now has one agent active on it.
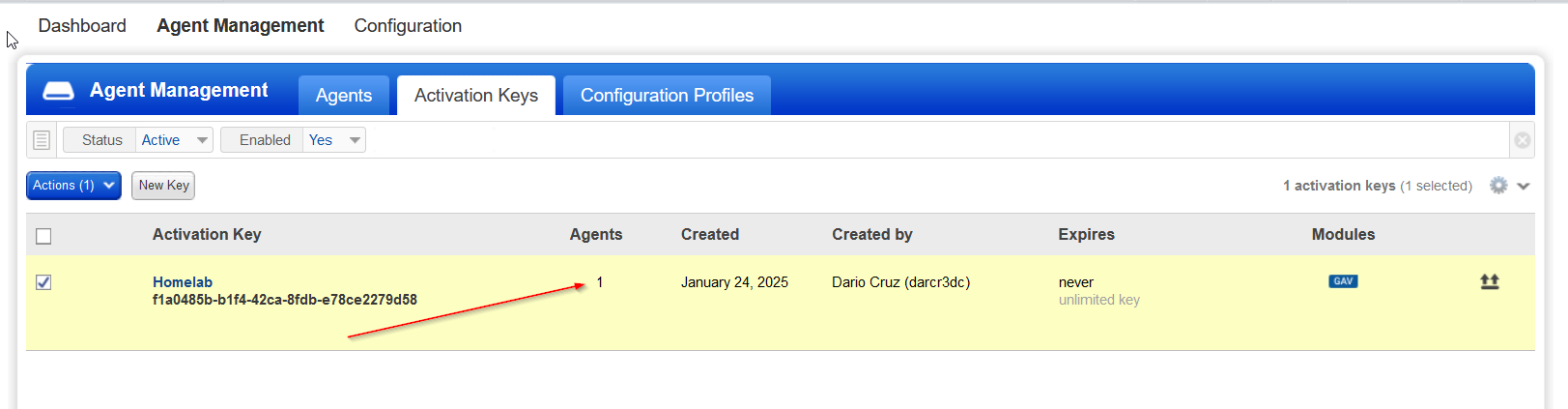
Going to the Agents section we also find that we have a our Vulnerable Windows 10 machine actively connected.
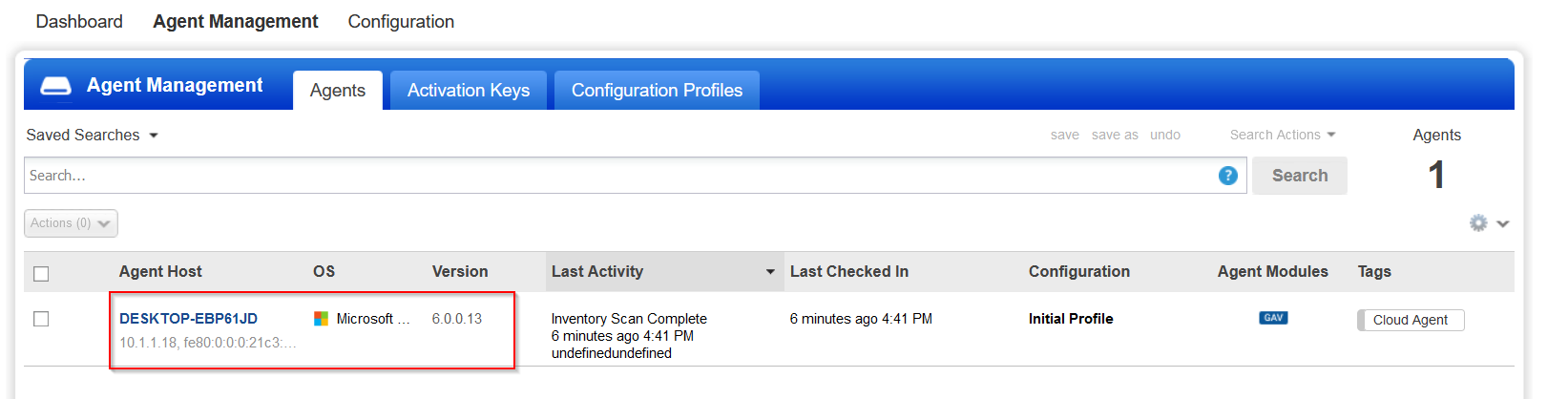
Lastly we need to activate the agent that we installed on our Windows machine for vulnerability management. It's very straight forward, from the Agents page select the agent, then click on the actions button and hit Activate Agent.
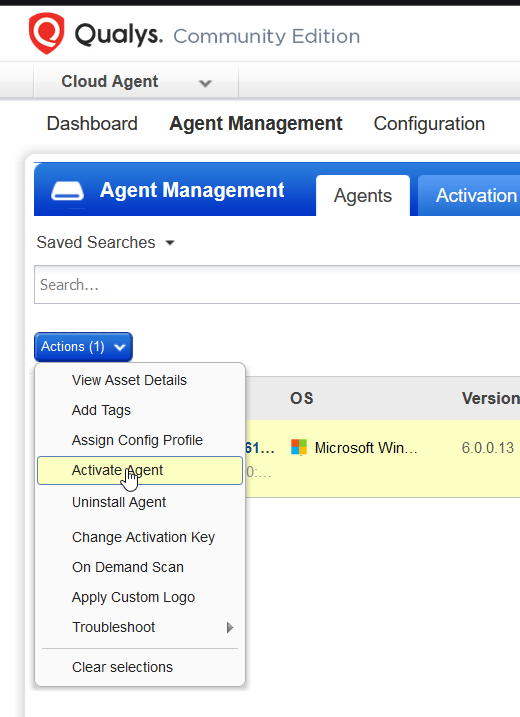
You will be presented with a Window prompting if you want to activate this agent for the Vulnerability Management module, select it and hit activate.
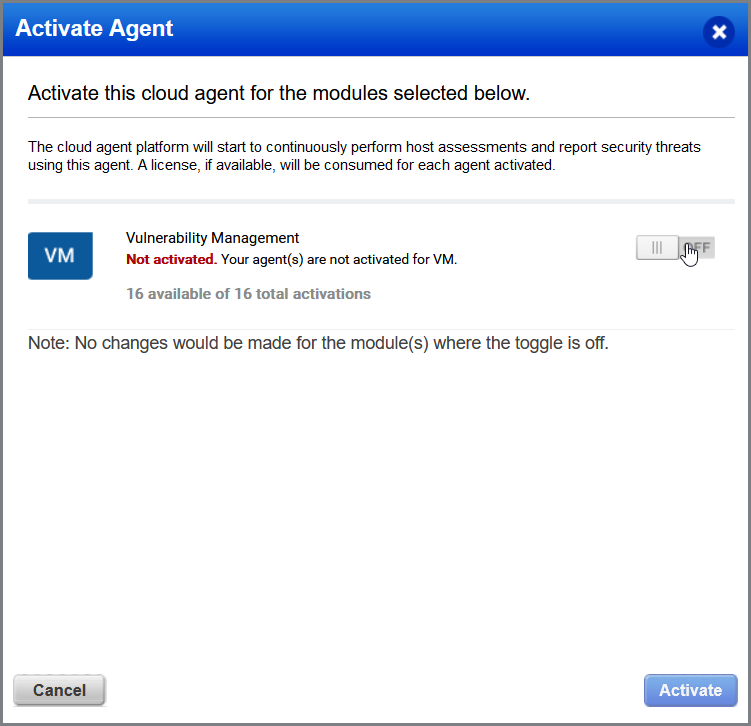
Now that we have added our agent to the vulnerability management module, Qualys is going to download the some files, specifically the vulnerability management manifest to the endpoints that have the agent installed. This can take some time to complete so I let Qualys sit for a bit and came back the next day. Looking at our list of agents from the agent management section, we can see that the manifest successfully downloaded and also that our first scan was run.
Agent Scanning & Results
Clicking on on our vulnerable windows machines hostname form the menu, we can see all of the information that has been populated from the agents initial scan and also from an scheduled vulnerability scan. Agents in Qualys are assigned configuration policies that dictate the cadence of scanning and the type of scanning that takes place. This agent was configured using the default configuration.
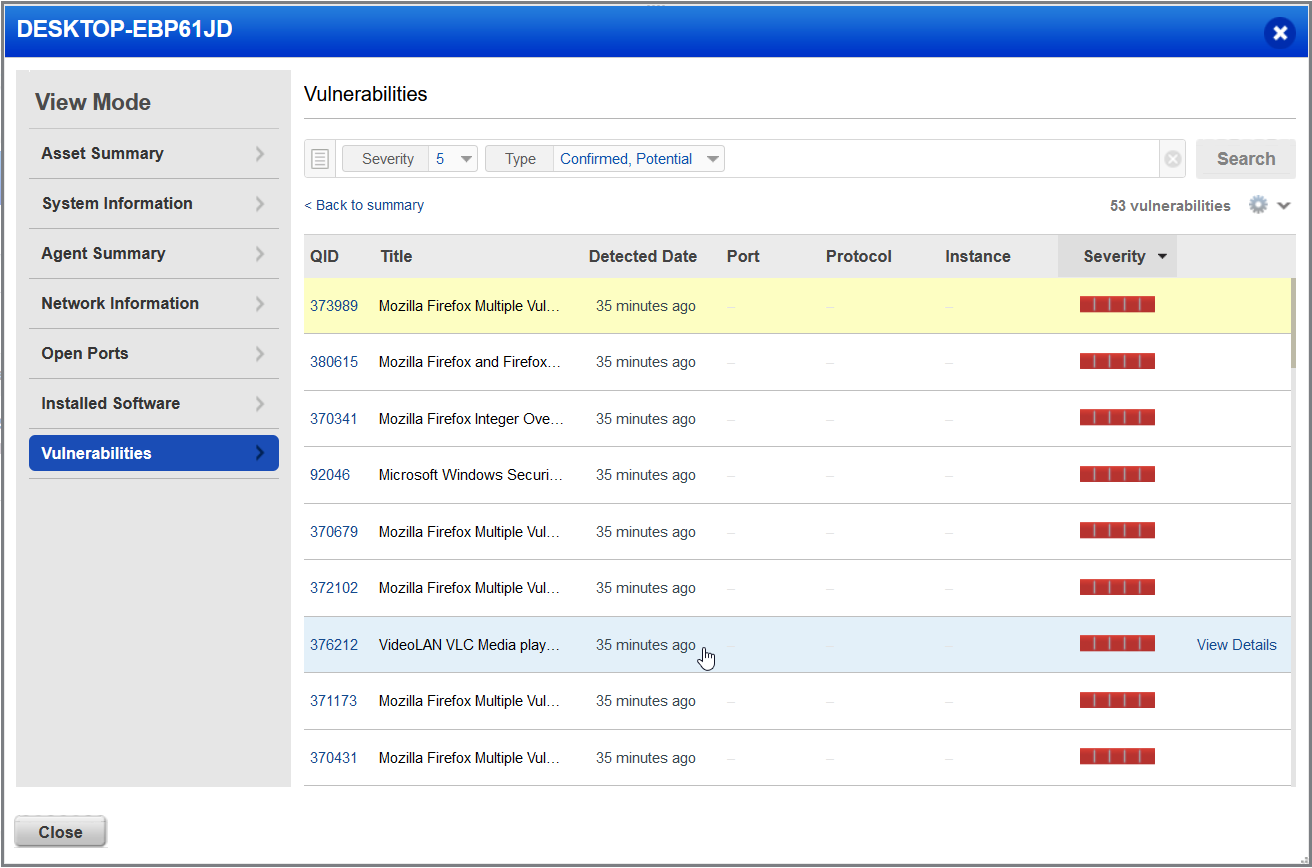
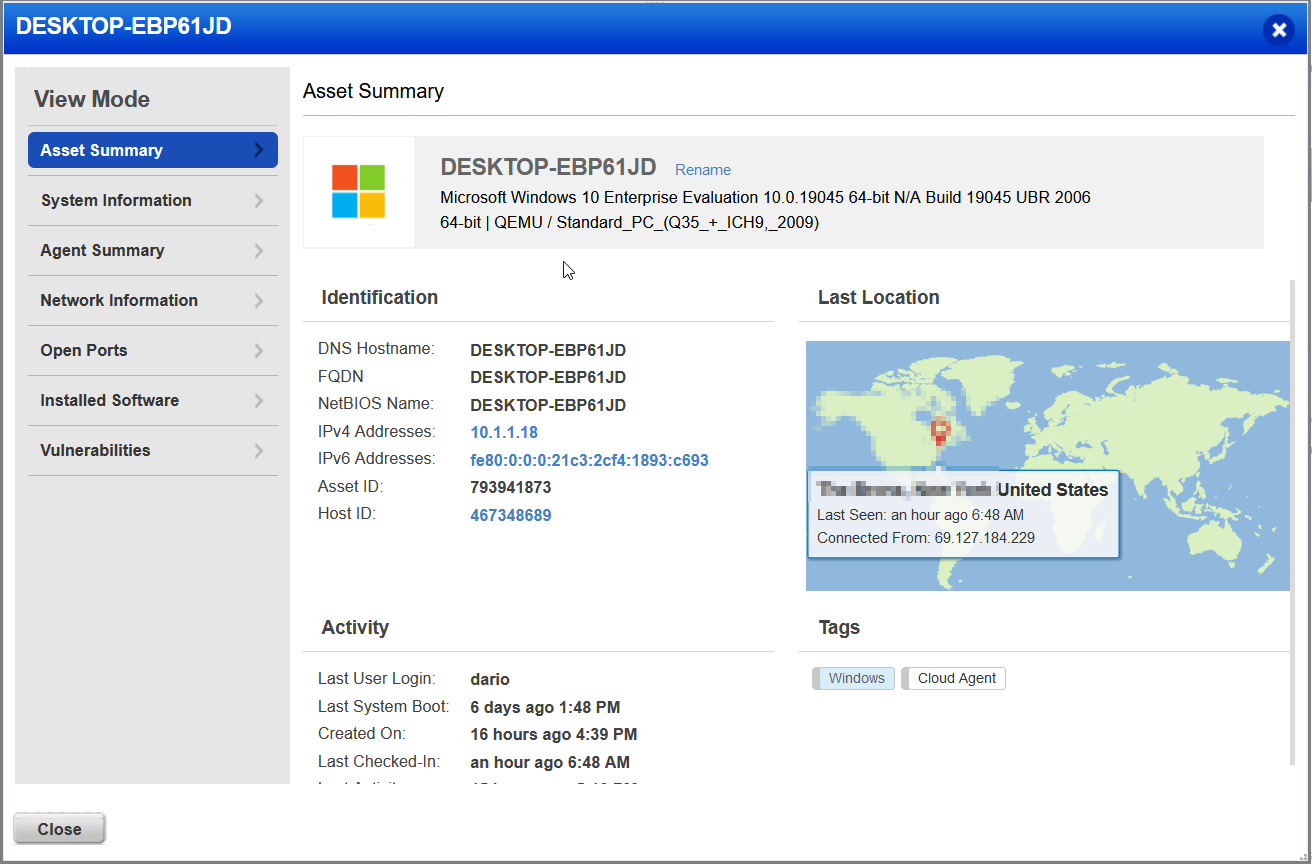 As you can see form the screenshot above, there is a lot of information that the Qualys agent software scans for, system info, network info, open ports, lists of installed software on the host, and most importantly, found vulnerabilities.
As you can see form the screenshot above, there is a lot of information that the Qualys agent software scans for, system info, network info, open ports, lists of installed software on the host, and most importantly, found vulnerabilities.
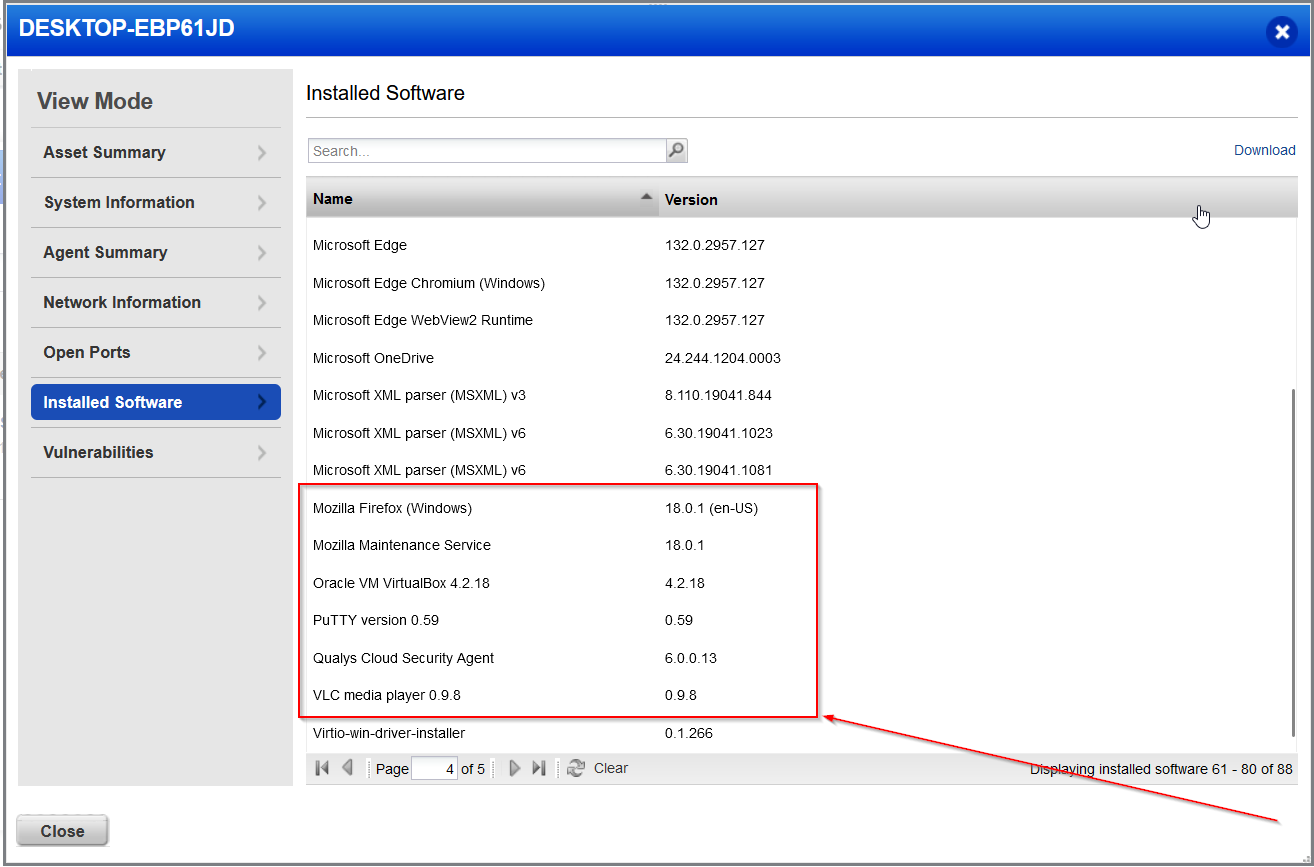
Looking at the installed software, we can see the old software that we installed on our Proxmox VM, which in should also lead to rather critical vulnerabilities being reported. The software versions installed are mostly from around 2013. 😆
Now for the vulnerabilities discovered, and yes we can see that Qualys has found 327 Critical Vulnerabilities. Ouch!
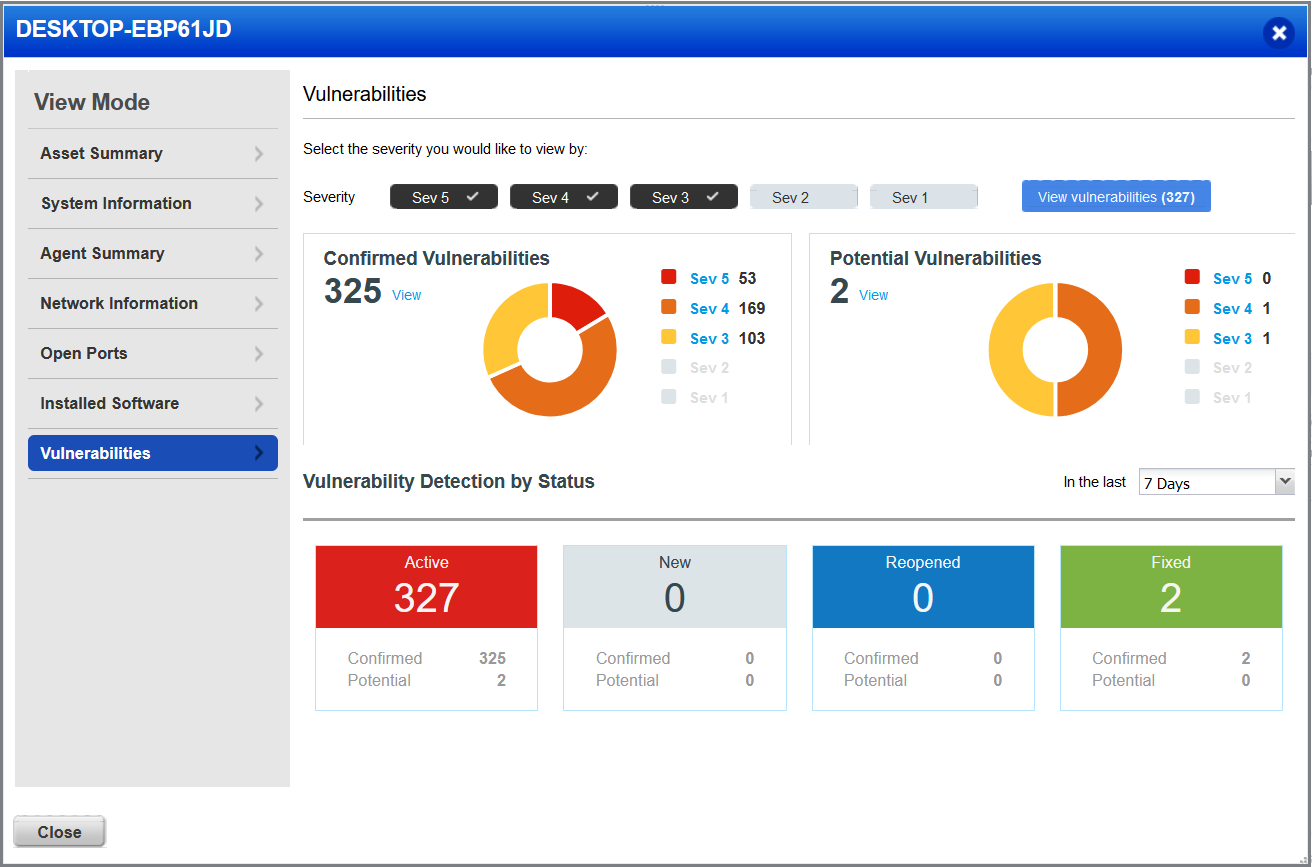
Digging deeper into the Vulnerabilities found, we can see a large amount of critical level 5 vulnerabilities form the outdated Firefox install, which makes sense as it interfaces with the open internet, and a few from VLC and also some from critical Windows updates not being installed.